
Vulnerabilities in a toy robot permitting snooping. Seriously
Our experts found that a popular children’s toy robot contained vulnerabilities allowing malicious actors to make video calls to it, steal the parental account, and modify the firmware.
221 articles

Our experts found that a popular children’s toy robot contained vulnerabilities allowing malicious actors to make video calls to it, steal the parental account, and modify the firmware.


The KeyTrap DoS attack, which can disable DNS servers with a single malicious packet exploiting a vulnerability in DNSSEC.

A vulnerability in the glibc library affects most major Linux distributions.

Time to update Fortra GoAnywhere MFT: an exploit has been developed for a critical vulnerability that allows attackers to bypass authentication and create admin accounts.

Ethical hackers told 37C3 how they found a few eye-openers while breaking DRM to fix trains.

Detailed analysis of Operation Triangulation, the most sophisticated attack our experts have ever seen, presented at 37C3 conference.

A serious vulnerability in UEFI firmware relevant to a large number of modern computers, and even servers.

A researcher has discovered a vulnerability in the Bluetooth protocol implementations for Android, macOS, iOS, and Linux, allowing devices to be hacked remotely.

Are Macs as safe as their owners think they are? A few recent stories about malware targeting macOS users.

Typical security issues of WordPress, and how they can be addressed to protect your website or online store from cybercriminals.

Bitcoin wallets created on online platforms between 2011 and 2015 may be insecure due to a vulnerability in the library for key generation.
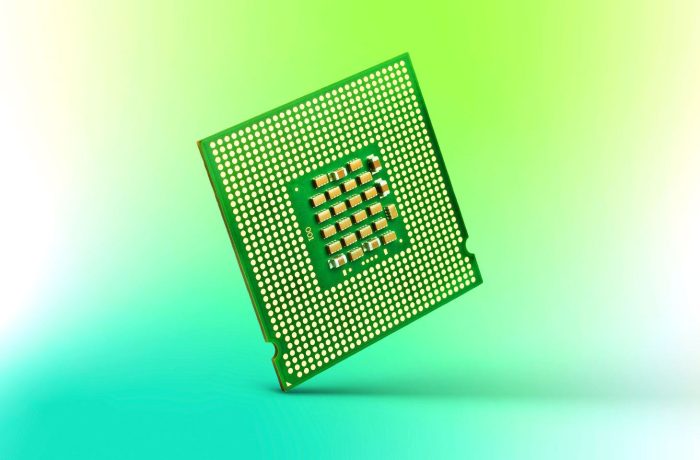
How a recently discovered bug in Intel processors threatens cloud providers.

A look at the pros and cons of updating Android — and ways to do it safely.

We discuss what zero-click attacks are, why they’re dangerous, and how to protect your company from them.

Mistakes commonly found in almost every large organization. What should the inforsec team look out for, and what protective measures should they take?

It’s time to update Confluence Data Center and Confluence Server: they contain a serious vulnerability that allows unauthorized creation of administrator accounts.

What personal information do modern cars collect about you, and how can you avoid surveillance or hacking of your vehicle?

We take a look at drivers: why we need them, the threats they pose, and how to keep your computer secure.

A few words on why desktop applications based on the Electron framework should be approached with caution.

Why the Windows system time can suddenly change, and how to stop it from happening.