More than half of companies use AI and IoT in their business processes
A recent Kaspersky study has revealed that more than 50% of companies have implemented Artificial Intelligence (AI) and Internet of Things (IoT) in their infrastructures. Additionally, 33% are planning to adopt these interconnected technologies within two years. Business owners must ensure they have the right caliber of cybersecurity solutions to secure them, experts recommend.
Interconnected technologies are the growing network of devices, systems and applications connected to the internet and each other. They transform enterprises, enabling them to gather more data and automate processes. But they also bring new risks and challenges when securing business assets and safeguarding customers.
Kaspersky conducted a study ‘Connecting the future of business’, which aims to help companies stay ahead of the changes interconnected technologies bring, posing critical questions regarding the way cybersecurity must adapt to them. For this purpose, the company surveyed 560 senior IT security leaders from North America, Latin America, Europe, Middle East and Africa, Russia and Asia-Pacific.
In this survey, Kaspersky sought to examine what respondents think of the following interconnected technologies:
- Artificial Intelligence (AI),
- Internet of Things (IoT),
- Augmented reality (AR), Virtual reality (VR) and digital twins,
- 6G and converged cloud networks,
- Web 3.0 which enables decentralized applications, blockchain smart contracts and user-managed data,
- Data spaces that enable seamless data sharing in collaborative settings.
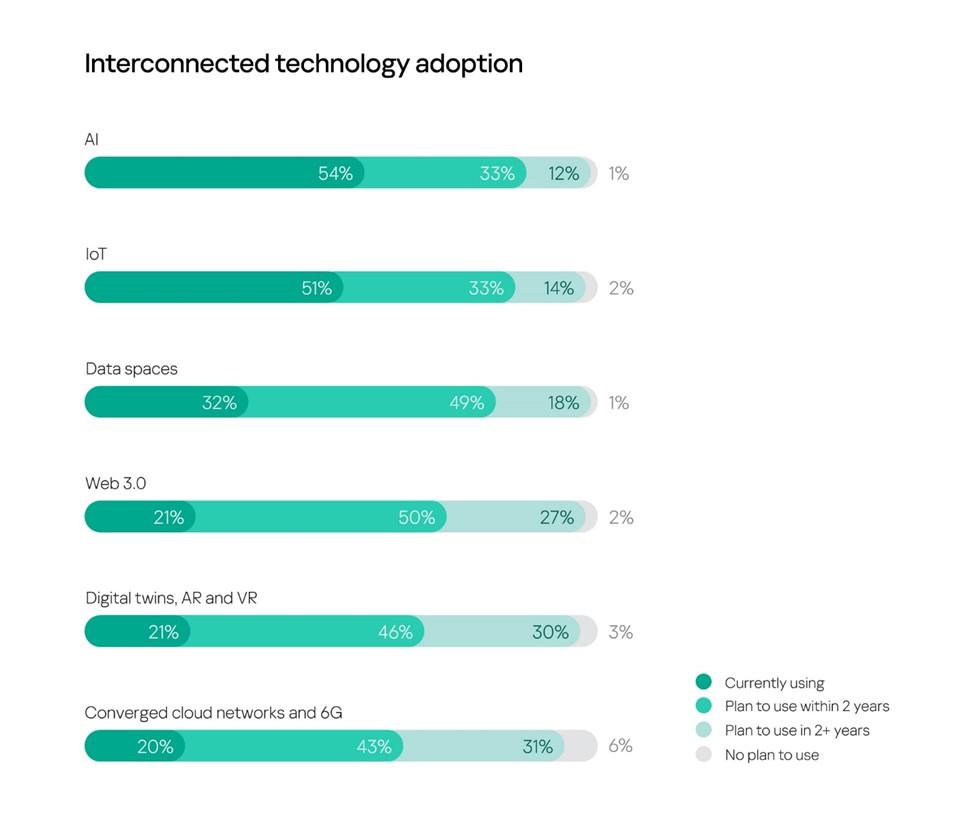
The research found that AI and IoT are already used by 54% and 51% of companies respectively. One in three plans to adopt them within two years. Data spaces are used by 32% of businesses, with nearly half (49%) intending to adopt them in the near future.
Other interconnected technologies (digital twins, AR, VR, web 3.0, 6G and converged cloud networks), are used by only one in five (20-21%) companies participating in the survey, but more than 70% are considering integrating them into their business processes soon.
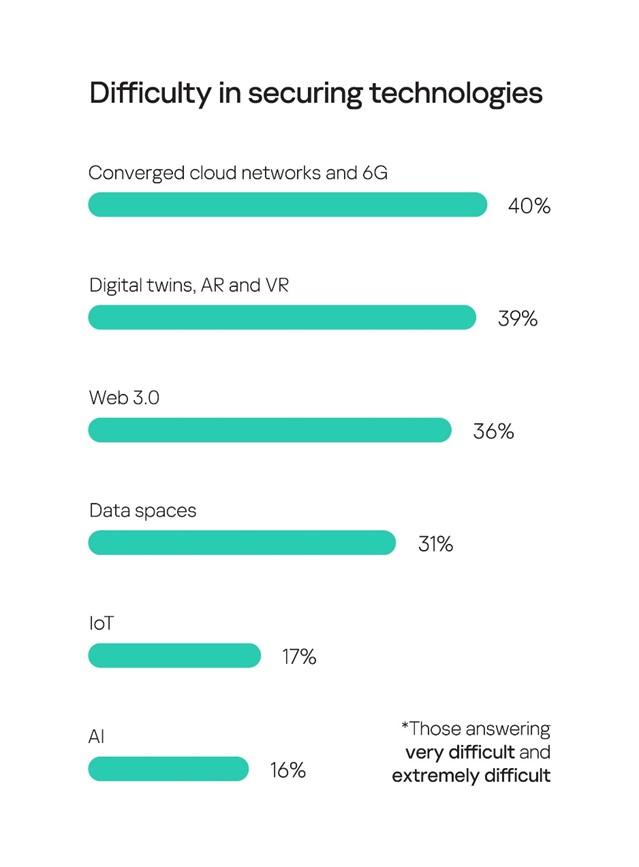
Because AI and IoT have become so widespread, they are vulnerable to new vectors of cyberattacks. According to the research, 16-17% of organizations think AI and IoT are ‘very difficult’ or ‘extremely difficult’ to protect, while only 8% of the AI users and 12% of the IoT owners believe their companies are fully protected.
However, as we can see, the less widespread the implementation of technologies, the more difficult it is for companies to protect them and vice versa. For instance, the least adopted AR/VR and converged cloud networks, are the most challenging technologies to protect in terms of cyber defense, with 39-40% of companies saying they are difficult to secure.
“Interconnected technologies bring immense business opportunities but they also usher in a new era of vulnerability to serious cyberthreats. With an increasing amount of data being collected and transmitted, cybersecurity measures must be strengthened. Enterprises must protect critical assets, build customer confidence amid the expanding interconnected landscape, and ensure there are adequate resources allocated to cybersecurity so they can use the new solutions to combat the incoming challenges of interconnected tech. Businesses integrating AI and IoT into their infrastructure need to protect it with Container Security and Extended Detection and Response solutions, to detect cyberthreats at early stages and provide effective defense,” comments Ivan Vassunov, VP, Corporate products, Kaspersky.
Given the scale of change that interconnected technologies is likely to bring, organizations must develop a strategy to implement and protect them. Based on the research findings, Kaspersky recommends four effective ways to ensure organizations are prepared to protect interconnected technologies:
1. Upgrade your cybersecurity solutions and use centralized and automated platforms such as Kaspersky Extended Detection and Response (XDR). As companies adopt interconnected technologies, they need cybersecurity solutions with more advanced features, enabling them to collect and correlate telemetry from multiple sources and provide effective threat detection and rapid automated response.
As many AI solutions are built on containers, it’s important to secure the infrastructure they are integrated in with cybersecurity products – such as Kaspersky Container Security – that allows companies to detect security issues at every stage of the app lifecycle, from development to operation.
2. Train and upskill your workforce. Building a cyber-aware culture requires a comprehensive strategy that empowers employees to gain knowledge and put it into practice. With Kaspersky Expert training, InfoSec professionals can advance their skills and defend their companies against attacks.
3. Meet regulations to avoid legal problems or reputational damage, by ensuring your cybersecurity practice meets changing standards and legal requirements.
4. Adopt secure-by-design principles. By integrating cybersecurity into each stage of the software development lifecycle, secure-by-design software and hardware become resilient against cyberattacks, contributing to the overall security of digital systems. Cyber Immune solutions based on KasperskyOS, for instance, allow companies to minimize the threat surface and significantly decrease the ability of cybercriminals to perform a successful attack.
The full report with additional findings on the interconnected technologies is available via the link.
More than half of companies use AI and IoT in their business processes
Kaspersky
Related Articles Press Releases
Companies state it takes more than 6 months to fill cybersecurity positions
The latest Kaspersky survey found that 48% of companies require over half a year to find a qualified cybersecurity professional. A lack of proven experience was cited as one of the biggest challenges, along with the high cost of hiring and global competition in talent acquisition.Read More >More than half of companies use AI and IoT in their business processes
A recent Kaspersky study has revealed that more than 50% of companies have implemented Artificial Intelligence (AI) and Internet of Things (IoT) in their infrastructures. Additionally, 33% are planning to adopt these interconnected technologies within two years. Business owners must ensure they have the right caliber of cybersecurity solutions to secure them, experts recommend.Read More >Kaspersky: more than 36 million AI & gaming credentials compromised by infostealers in 3 years
Staggering amounts of stolen login credentials were discovered by Kaspersky Digital Footprint Intelligence experts as they conducted an analysis in light of the Mobile World Congress 2024.Read More >
We use cookies to make your experience of our websites better. By using and further navigating this website you accept this. Detailed information about the use of cookies on this website is available by clicking on more information.