In April 2016 a young and ambitious trojan cryptor known by the name CryptXXX was released. It was distributed by the infamous Angler and Neutrino exploit kits. It’s creators certainly hoped that after the release they could lay on the couch and watch the money flow from the victims pockets to their bitcoin wallets. But things did not go the way they had expected.
A few days after the CryptXXX trojan was discovered, experts from Kaspersky Lab found a mistake in CryptXXX file encryption algorithms and thus were able to create a cure. A free utility called Rannoh decryptor could be used to decrypt files, encrypted by CryptXXX.
The criminals had to get up from their comfortable couch and start working to fix the bug. So they started distributing a new version, but it took our experts just a few days more to invent a cure for the second version of CryptXXX. Rannoh decryptor was updated — and the Trojan’s victims could once again decrypt their files without paying ransom.
#CryptXXX v2 can now be decrypted with our decryptor #noransom #ransomware #infosec https://t.co/XJZGaQK0E7 pic.twitter.com/3D1SmdiCeM
— Kaspersky Lab (@kaspersky) May 13, 2016
With their latest versions thwarted, the criminals abandoned relaxation and created a third version of their ransomware, hoping that nobody would be able to find a way to make a decryptor.
They almost succeeded. For a rather long period of time CryptXXX v.3 was able to terrorize people all over the globe, encrypt their files and demand ransom to bring them back. It was also capable of stealing credentials from different applications.
The distribution of the new version started in May, and our experts estimate that there may be several hundred thousand infected users. Kaspersky Lab’s products alone detected and prevented about 80,000 attempts to infect computers with CryptXXX v.3. Almost a quarter of all attacks were targeting users from USA, with Russia, Germany, Japan, India and Canada combining for another 28% of infection attempts.

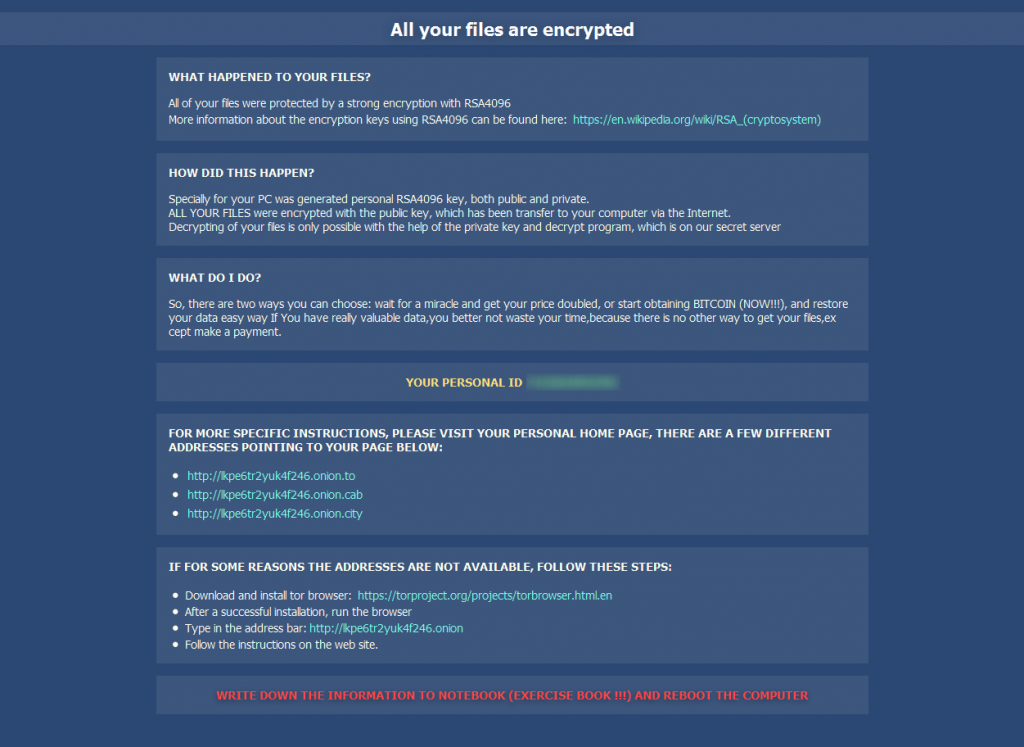
The ransom demand message varies depending on the version of the CryptXXX trojan, but usually it similar to these examples
But nothing lasts forever. Today we’re happy to announce that our researchers have managed to find a cure for the third version of CryptXXX trojan, so the .cryp1, .crypt and .crypz files can be decrypted once again. We’ve added the decryption to the Rannoh Decryptor utility, which you can find either at our website or at NoMoreRansom.org.
If you were hit by CryptXXX — visit one of the aforementioned websites, download the utility and get your files back. Our utilities are free, and can help you recover files encrypted by most versions of the trojan, so you would save a nice sum by not paying the ransom to the criminals.
“Our regular advice to the victims of different ransomware families is the following: even if there is currently no decryption tool available for the version of malware that encrypted your files, please don’t pay the ransom to criminals. Save the corrupt files and be patient — the probability of a decryption tool emerging in the near future is high. We consider the case of CryptXXX v.3 as proof of this advice. Multiple security specialists around the world are continuously working hard to be able to help victims of ransomware. Sooner or later the solution to the vast majority of ransomware will be found,” — said Anton Ivanov, security expert at Kaspersky Lab.
Our other advice is to think proactively and protect yourself in advance. It’s much more convenient not to get your files corrupted in the first place. To do this, follow these two simple steps:
1. Back up your data regularly on a detachable media that is not kept connected to your computer all the time.
2. Install a good security solution. By the way, recent independent studies showed that Kaspersky Internet Security is extremely good against ransomware.
 Ransomware
Ransomware

 Tips
Tips